Excel crtice
Kako u ćeliji Excel-a ukloniti zadnju cifru broja : =TRUNC(A1/10) gde je A1 problematična ćelija. link Kako broj u ćeliji...

HowTo za Linux, WIN, Heklanje i Kuhinjske recepte. Prodaja hekleraja :-)
Kako u ćeliji Excel-a ukloniti zadnju cifru broja : =TRUNC(A1/10) gde je A1 problematična ćelija. link Kako broj u ćeliji...
Slučajno je ispalo da liči na Duolingo sovicu :-)
Ako se radi upit za broj, dati broj MORA biti između BAŠ OVAKVIH navodnika : where Broj = '00123' Napomena...
Isheklane od najlonskog tankog konopca. Ove dve su za manje saksije : Evo kako to izgleda u upotrebi : A...
Veliki i širok Slytherin šal, za sada na pola gotov : Planiram da na krajeve dodam kićanke, i da ga...
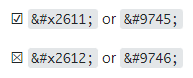
U RedMine Wiki je prilično komplikovano staviti specijalne simbole. Ne mogu se staviti kao :smiley: jer to ne prihvata. Ne...
Kako obrisati temp fajlove na WIN 10 mašini : 1. On your keyboard, press the Windows + R keys at...
Kako videti koji su fajlovi otvarani u zadnjih nekoliko dana? Otići na lokaciju : C:\Users\mojnalog\AppData\Roaming\Microsoft\Windows\Recent i videćeti ih! Poređati po...
Isheklala sam kapicu od deblje vunice, i ukrasila je srcićima :
Lepo mesto, lep odmor. Lepe svari : Lepa glavna ulica za šetnju, prepuna restorana Lepe dve sporedne ulice sa gomilama...